Vijay C Roy
Tribune News Service
Chandigarh, May 20
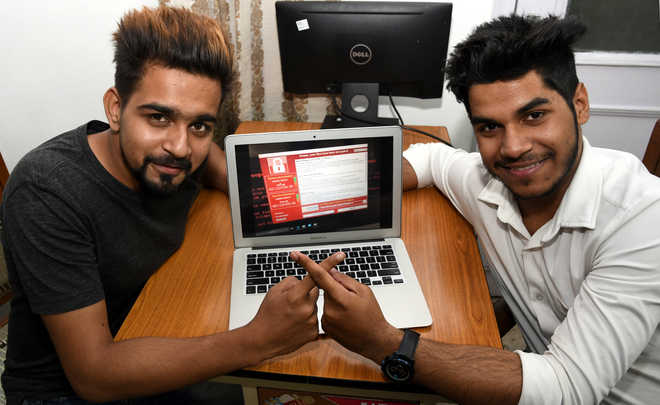
Two students of a Punjab-based private university claimed to have worked out a solution to ransomware. BhavKaran Singh and Dev Aggarwal, fourth semester students of Chandigarh University and pursuing computer science engineering, said an affected device could easily be restored by following simple steps.
Ransomware attack locks a device, such as a computer, tablet or smartphone and then demands a ransom to unlock it.The software is normally contained within an attachment to an email that masquerades as something innocent. Once opened, it encrypts the hard drive, making it impossible to access or retrieve photographs, documents or music. The attack has so far been reported from Gujarat, Odisha, West Bengal, Andhra Pradesh and Maharashtra. “We have been closely following reports pertaining to the ransomware attack and decided to work on it. On an average, we used to work for eight-10 hours daily, especially at night. An affected laptop can be easily be restored now,” said Bhav Karan
BhavKaran Singh is also a certified ethical hacker, certified cyber security analyst, part-time freelancer and developer.
Clean ransomware
- Ransomware files cannot be removed directly as they are still working in the background in many unknown service names.
- To remove the virus
- Go to Windows safe mode by pressing (F8 key on the keyboard) during computer boot screen
Find ransomware files
- @WanaDecryptor@ n @Please _Read_Me@ n @WanaCry
To recover files
- Right click on the folder you want to recover, then click on properties
- Select ‘Restore Previous Version’ tab
- Click on restore and your infected files will be recovered
- However, cyber experts say infected files can be recovered only if the system restore option is enabled and in a majority of cases, users don’t enable it. So it is advisable that the user must enable the system restore option.
Precautionary measures
- Do not open unwanted attachments in mail
- Don’t click a link in an email unless you are 100% certain.
- Don’t open or respond to emails that look suspicious
- Ignore attachments that you aren’t expecting, especially if you don’t know the sender.
- Don’t give personal details or fill in forms. If you get a notice from a financial institution stating that you need to upgrade your details or change your password, don’t follow the instructions, but go directly.
Unlock Exclusive Insights with The Tribune Premium
Take your experience further with Premium access.
Thought-provoking Opinions, Expert Analysis, In-depth Insights and other Member Only Benefits
Already a Member? Sign In Now